Lessons Unlearned, Countermeasures Unmeasured
Written By: Max Briggs, Vice President, Chesley Brown International
The first rule of open-air event security sounds simple: control what you can see, and see what you can’t control. In practice, many plans still concentrate almost entirely at ground level—perimeter fencing, magnetometers, bag checks, crowd management—while leaving rooftops, upper windows, and high balconies to chance. That blind spot is not theoretical. Decades of painful case histories show that elevated positions repeatedly give attackers time, angle, and concealment, enough to convert a routine program into a crisis in seconds.
The pattern is consistent. The countermeasures are neither exotic nor expensive. What’s missing is the will to make rooftop access control a baseline, not an afterthought.
The Problem We Keep Re-Learning
Security teams are excellent at what they train for. Ground-level threats are intuitive and visible; vertical threats are not. In walkthrough after walkthrough, we still find:
- Unmonitored rooftops and sightlines overlooking stages, procession routes, or gathering points.
- Event plans that assign dozens of personnel to entries and concourses but lack any dedicated elevated overwatch.
- Staffing ratios calibrated to crowd size rather than to the geometry of the venue and its surrounding structures.
- Underuse of simple tools: a pair of binoculars, a pre-event rooftop sweep, that could transform risk overnight.
In other words, we invest heavily in what’s in front of us and underinvest in what’s above us.
Why Elevated Positions Change the Math
Elevation confers three advantages to an attacker: time, perspective, and concealment.
- Time because the attacker is less likely to be jostled or noticed by a crowd.
- Perspective because a high angle expands fields of fire and observation.
- Concealment because the more distance and structure between an attacker and responders, the harder it is to localize a threat.
Security teams under duress tend to look toward the sound and motion of the crowd, not up. It’s a human reaction, and a predictable one. This is precisely why “vertical threat assessment” must be explicit in the plan, staffed, and rehearsed.
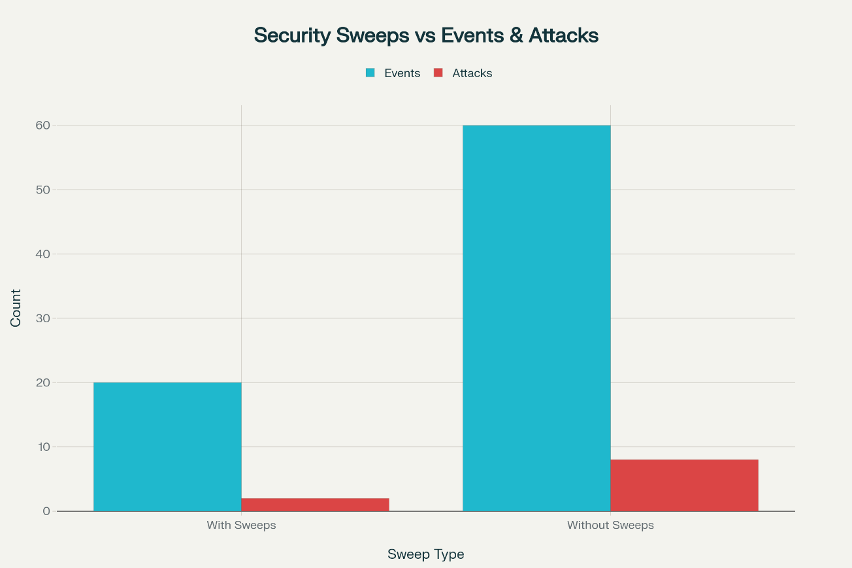
What Rooftop Access Control Actually Means
Rooftop access control isn’t a single device or a one-size program. It’s a layered approach that blends policy, physical measures, optics, and live monitoring.
Pre-event vertical survey
Before a single barricade goes up, the security lead should identify every potential elevated vantage point with line-of-sight to critical event assets like the stage, procession route, VIP ingress/egress, media positions, and densely occupied areas.
Ownership and permissions
Elevated vantage points frequently sit on third-party property, private rooftops, campus buildings, municipal structures. Plans should include event-day access agreements with facilities owners to enable temporary lock-outs, controlled access, or escort-required entry during the event window.
Physical and procedural controls
On event day, roof hatches and service doors that aren’t needed should be locked and verified; needed ones should be staffed. Temporary signage and roped-off areas discourage curiosity and inadvertent access. Where property owners permit, lightweight barriers or sensor-enabled door controls can help. Add a radio call-sign to each roof access point so ground teams can request checks by location without confusion.
Overwatch and observation
Two simple, low-cost measures provide outsized benefit: binocular spotters and camera coverage. Dedicated spotters conduct a sweep before the gates open and then rotate during the event. They look for rooftop movement, windows suddenly opened on upper floors, and unexpected silhouettes at parapets and ledges. Pair that with temporary cameras on friendly rooftops to cover wide areas and push real-time feeds back to the command post.
Aerial perspective
Where regulations, weather, and air-rights permit, drones are powerful force multipliers. A tethered drone offers persistent, stable imagery over the venue footprint; free-flying assets can sweep adjacent roofs and high windows on a pre-planned route. Modern systems integrate simple analytics like person/vehicle detection, heat-mapping, anomaly flags to help small teams focus on what matters rather than staring at screens. And if the airspace is restricted or drones are impractical, binoculars and well-placed cameras remain the backbone.
Legacy Ratios vs. Risk-Based Staffing
One reason vertical threats persist is the inertia of budgeting by headcount ratios (“one officer per X attendees”). Ratios are an easy planning shorthand but a poor proxy for venue-specific risk. An open campus quad with three adjacent mid-rises demands a different deployment than a fenced fairground surrounded by single-story structures even if attendance is identical.
Risk-based staffing weights the plan to geometry, elevation, and approach vectors, then assigns people and sensors accordingly. A useful rule of thumb is to treat every approachable rooftop with direct sightline as part of your inner perimeter. That means it gets one or more of the following: pre-event sweep, locked/verified access points, live observation, patrol/response capability, and an owner contact on the comms plan.
What Good Looks Like on Event Day
Before gates open: A vertical sweep clears all nearby roofs and visible upper floors. Radios confirm which doors are locked, which are staffed, and where temporary cameras are live. The command post has a city-block map with rooftops labeled and assigned. Aerial assets run a brief pattern to capture baseline imagery.
While underway: Spotters rotate through positions to maintain fresh eyes. PTZ operators scan slow, deliberate arcs over rooflines and upper floors. If a window that was closed is now open or if a parapet silhouette appears an “eyes on” call prompts a focused camera check and, if needed, a nearest-unit verification.
If an anomaly is detected: The plan prioritizes verification over speculation. A two-step drill: observe, confirm prevents unnecessary crowd disruption while still enabling a rapid response. If the concern escalates, the vertical team calls for ground interdiction to the specific access point.
After closing: The vertical team conducts a final sweep and relays a simple checklist back to command (all access points sealed as found, no remaining persons on roofs, temporary equipment retrieved). Those logs, combined with any alerts or observations, feed a quick debrief: what we saw, what we learned, what we’ll adjust.
The Tools Are Not the Hurdle
A persistent myth is that elevated-threat mitigation requires specialized counter-sniper teams or a permanent camera grid. In reality, a compact kit that includes binoculars, a few quick-deploy cameras, and (where lawful and appropriate) a tethered or small free-flying drone, covers the majority of venues. The affordability and portability of these tools is precisely why they should be standard.
The most important “technology” remains a repeatable process. Plans that institutionalize pre-event rooftop surveys, define who controls which access points, and rehearse elevated-threat communications outperform those that treat rooftops as an edge case.
Venue Selection: Eliminate Risk Before You Inherit It
Sometimes the best mitigation is choosing a different location. When planners have latitude, favor sites where adjacent elevation is either inherently controlled (single-story surroundings, clear setbacks) or contractually controllable (owners willing to lock, staff, or monitor roofs during the event window). Where the venue is fixed—tradition, permits, community priorities—scale countermeasures to match the complexity of the skyline. This is not about creating a fortress; it’s about aligning resources with real-world geometry.
Why Many Plans Still Fall Short
If the countermeasures are straightforward, why do elevated attacks still puncture the headlines? Three reasons, all fixable:
- Ownership gaps: No one “owns” the roof. It sits in a grey zone between facilities, the event operator, and law enforcement. The fix: assign a vertical-security lead and write third-party access agreements into your advance. A Fractional CSO can help you navigate of any competing priorities that may show up.
- Budget optics: Leaders prefer visible security investments (gates, magnetometers) that reassure attendees. Overhead observation is less visible, so it gets cut first. The fix: quantify the risk reduction in terms executives understand—response time and incident probability and bake it into board-level risk acceptance.
- Process debt: Teams copy last year’s plan, which copied the plan before that. The fix: require a vertical-threat checklist on every planning template; treat it like medicals or radio checks: boring, mandatory, and lifesaving.
The conclusion from years of after-action reports is unambiguous: the tools and techniques required to prevent such tragedies are basic, proven, and overdue for systematic adoption.
| Tool/Method | Primary Function | Deployment Guidance | Cost/Complexity |
|---|---|---|---|
| Drones (tethered or freeflight) | Live full-area aerial surveillance | Pre-plan, integrate with command | Moderate–High |
| Rooftop HD PTZ cameras | Wide-angle, stable monitoring | Quick-deploy or permanent | Moderate |
| Binocular/manual sweeps | Low-cost, direct visual inspection | Trained spotters | Low |
| Mobile surveillance towers | Temporary vertical coverage | At perimeters/access points | Moderate |
What We Recommend (and Deliver)
Chesley Brown’s role is to close this gap without over-engineering your event. Our teams design and execute vertical-threat programs that are proportionate, lawful, and repeatable:
- Pre-event vertical risk assessments that map every line-of-sight to your critical assets and convert them into access-control and monitoring tasks.
- Temporary rooftop monitoring packages: quick-deploy cameras with secure feeds into your command post; where permitted, tethered and free-flying drone operations with pre-planned sweep routes.
- Manual sweep and spotter programs using trained observers with binoculars to ensure continuity in no-drone or restricted zones.
- Access-control coordination with building owners to lock or staff roof hatches, service doors, and high-risk windows for the event window.
- Threat-based staffing models that replace legacy ratios with geometry-driven deployments.
- Tabletop exercises and live drills so your vertical team knows exactly how to verify, escalate, or resolve an anomaly without creating new risks on the ground.
- Run a Protective Intelligence report on any public speakers, performers, or guests the event will host. This will allow you to understand the unique risk landscape each individual has.
This approach scales from city-block parades to campus ceremonies and corporate festivals, because it aligns resources with reality: the threat is three-dimensional.
A Final Word
We don’t need to name past tragedies to learn from them. The lesson is the same each time: events are vulnerable where the plan doesn’t look up. Rooftop access control and elevated-position monitoring are not special-occasion add-ons; they are the cost of doing public safety well. The sooner organizations standardize them, the sooner “lessons learned” stop being a euphemism for “lives lost.”
Call to Action
If your outdoor or open-air events don’t already include a vertical-threat program with pre-event rooftop surveys, access agreements, elevated monitoring, and a drilled response plan, now is the time to fix that. A 30-minute review with our team will show you exactly what’s missing and how to close the gap before your next event.
When your name is on the door, risk is personal. We’ll help you raise the standard, literally and figuratively.
Sign up!
For industry-leading guides and analysis sign up for our blog below.
Latest News
From Headlines to Early Warnings: How Real-Time Intelligence Shields Organizations From Tomorrow’s Crises
At 8:11 a.m., the regional COO’s phone lit up with a text from a site manager: “There’s a crowd forming outside the Atlanta distribution center – looks like a protest.” By the time the security…
Read MoreThe IoT Security Nightmare: Why Smart Buildings Are a Hacker’s Playground
Picture the Scene On a Tuesday morning in downtown Chicago, tenants in a new office tower swipe their badges at the glass entrance doors. Inside, the lobby lighting adjusts automatically to the growing crowd. Elevators,…
Read MoreWhite-Collar Crime: How to Detect and Prevent Fraud in Your Business
Fraud rarely announces itself with flashing lights. It works quietly, exploiting gaps in oversight, trust, and accountability until the numbers no longer add up. In 2023, a regional finance firm learned this lesson the hard…
Read MoreFrom Ports to Warehouses: Securing the Supply Chain in 2025
Summary: The Human Side of a Global Problem It started with a call just before sunrise. A regional operations manager learned a high-value shipment never made it from the port to the warehouse. The truck…
Read MoreSpot the Signs: Preempting Workplace Violence Through Intelligence
Learn to recognize pre-threat behavioral indicators and prevent workplace violence with intelligence and proactive risk management strategies.
Read More





